How Bitcoin Prevents Double-Spending: Inside the Blockchain Solution
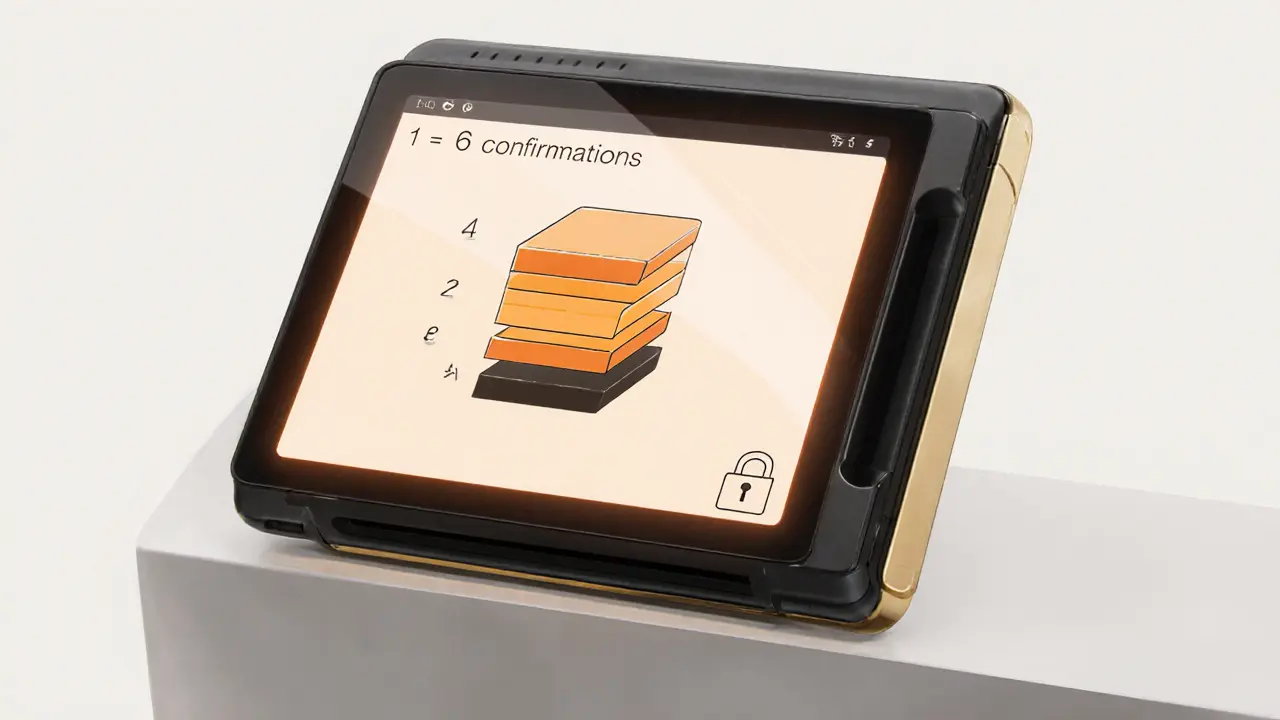
Bitcoin Confirmation Calculator
How Many Confirmations Do You Need?
Enter your transaction value to see the recommended number of confirmations needed to prevent double-spending attacks.
When Bitcoin entered the scene in 2009, it tackled the biggest flaw in digital cash: the ability to spend the same token twice. That flaw, called double-spending, would make any electronic currency worthless if not stopped. Below we break down exactly how Bitcoin blocks this cheat, step by step, and why the solution still works after more than a decade.
What is Double-Spending and Why It Matters
In a traditional database, a central authority (like a bank) records every debit and credit, making sure the same dollar isn’t sent to two places at once. Digital tokens, however, are just bits of data. Without a trusted ledger, a malicious user could copy that data and broadcast two identical transactions - a classic double-spending attack.
For a currency to hold value, it must be scarce. If anyone could duplicate coins at will, scarcity disappears and confidence evaporates. That’s why solving double-spending is the linchpin of any credible cryptocurrency.
Bitcoin’s Core Ingredients
Bitcoin’s answer combines three pillars:
- Blockchain - an immutable chain of blocks that records every transaction in chronological order.
- Proof of Work (PoW) - a computational puzzle that miners must solve to add a new block.
- Miner incentives - block rewards and transaction fees that reward honest work.
These pieces work together to create a distributed ledger that no single party can rewrite.
How the Blockchain Stops Duplicate Coins
Every block contains a batch of transactions. Each transaction points to a previous unspent output (UTXO) that proves where the coins came from. Because the blockchain is chronologically ordered, the network can always decide which transaction happened first.
The chain is linked by cryptographic hashes: each block stores the hash of its predecessor. Changing any transaction in an old block would alter its hash, which would instantly break the link to the next block. All nodes would reject the tampered chain, making retroactive changes practically impossible.
Proof of Work: The Economic Brake
When a miner finds a valid PoW solution, they broadcast a new block. The solution proves that the miner invested real computational work - roughly 400 exahashes per second across the network in 2024. To override the honest chain, an attacker would need to control more than 50% of that power, a cost measured in billions of dollars worth of hardware and electricity.
This economic barrier is what makes double-spending prohibitively expensive. Even if a hacker managed a brief “51% attack,” they could only rewrite a few recent blocks before the honest miners outpace them again.

Transaction Lifecycle: From Mempool to Finality
When you click “send,” your transaction first lands in the Mempool. Nodes check that the inputs haven’t been spent already. If they’re clean, the transaction waits for a miner to include it in a block.
Once a block is added, the transaction gets its first Confirmation. Each subsequent block adds another confirmation, raising the security exponentially. The community convention is to wait for six confirmations for high‑value payments - by then, reversing the transaction would require redoing the PoW for six blocks, a near‑impossible task.
During the unconfirmed period, attackers sometimes try “replace‑by‑fee” (RBF) to swap a low‑fee transaction with a higher‑fee one. Modern wallets let merchants set policies that either accept or reject RBF‑eligible transactions, giving extra control over risk.
Why Bitcoin Beats Traditional Systems
Credit‑card networks rely on a central processor that can roll back or dispute a payment. That central point is both a convenience and a vulnerability - it enables chargebacks and creates a single point of failure. Bitcoin removes that middleman entirely.
Because the ledger is public, anyone can verify that a transaction has not been spent elsewhere. No trust in a third party is needed; cryptographic proof does the job.
Real‑World Checks: How Merchants Protect Themselves
If you run an online store, here’s a quick checklist to minimize double‑spending risk:
- Require at least one confirmation for low‑value items (< $10).
- Require three to six confirmations for anything over $100.
- Configure your wallet to reject RBF‑enabled transactions for high‑value sales.
- Monitor the Mempool for sudden fee spikes that could signal an attack.
- Use a reputable payment processor that automatically handles confirmation thresholds.
Following these steps keeps your revenue safe without needing a bank.
Advanced Protections and Future Trends
Researchers keep probing Bitcoin’s security. Recent upgrades include better mempool management and stricter RBF policies. Lightning Network users rely on off‑chain channels, which add another layer of finality after the underlying Bitcoin transaction is confirmed.
As the hash rate climbs, the cost of a 51% attack grows, further cementing the network’s resistance to double‑spending. Even quantum‑computing threats are being studied, but for now the economic moat remains the strongest defense.
Quick Comparison: Bitcoin vs Traditional Payment Systems
| Aspect | Bitcoin | Bank/Card Network |
|---|---|---|
| Ledger Type | Public, immutable blockchain | Private, centrally controlled database |
| Verification Method | Proof of Work consensus | Trusted third‑party validation |
| Cost to Attack | Billions of dollars in hardware & electricity | Relatively low - exploits of software bugs or insider fraud |
| Transaction Finality | Irreversible after 6 confirmations | Reversible via chargebacks |
| Transparency | All transactions publicly auditable | Opaque - only the bank sees full data |
Summary of the Core Mechanisms
In a nutshell, Bitcoin stops double‑spending by:
- Recording every transfer on a single, ordered blockchain.
- Requiring miners to solve PoW puzzles, making rewrites economically suicidal.
- Using UTXO references so each coin can only be spent once.
- Adding confirmations that exponentially raise the cost of reversal.
- Providing a public, trust‑less system where anyone can verify the ledger.
The result is a money system that works without banks, without chargebacks, and without the classic double‑spending loophole.
What exactly is double‑spending?
Double‑spending is the act of using the same digital token in two separate transactions. If unchecked, it would destroy trust in any electronic currency.
How does the blockchain guarantee transaction order?
Each block contains a cryptographic hash of the previous block. This chain forces every node to agree on a single chronological sequence, so the first transaction in the chain is always the valid one.
Why are six confirmations the standard for large payments?
Every new block adds another layer of PoW work that an attacker must redo to overturn a transaction. After six blocks, the required computational effort becomes astronomically high, making a successful double‑spend virtually impossible.
Can a 51% attack enable double‑spending?
In theory, controlling over half the network’s hash rate lets an attacker rewrite recent blocks and double‑spend. In practice, achieving and sustaining that power costs billions, far outweighing any potential profit.
What is Replace‑by‑Fee (RBF) and how does it affect security?
RBF lets a sender broadcast a higher‑fee version of an unconfirmed transaction, replacing the original. Merchants can mitigate risk by rejecting RBF‑enabled transactions for high‑value sales or waiting for additional confirmations.
How do miners earn rewards and why does that matter?
Miners receive a block subsidy plus transaction fees for each block they add. These incentives align their financial interest with keeping the ledger honest, because a successful attack would jeopardize their own earnings.


Jessica Pence
October 20, 2025 AT 08:05Bitcoin’s blockchain really does the heavy lifting against double‑spending.
johnny garcia
October 20, 2025 AT 19:12Indeed, the immutable ledger, secured by proof‑of‑work, provides a mathematically provable order of transactions, rendering duplication infeasible. 😊
Ryan Comers
October 21, 2025 AT 06:19Sure, it sounds solid, but what if a rogue nation just marshals enough hash power and decides to rewrite history anyway?
Prerna Sahrawat
October 21, 2025 AT 17:25One must appreciate the sheer elegance with which the Bitcoin protocol orchestrates a symphony of cryptographic primitives, each meticulously designed to reinforce the others in a harmonious balance that precludes the specter of double‑spending.
At the heart of this architecture lies the blockchain, an append‑only data structure whose very immutability is guaranteed by the hash of each preceding block, thereby creating an unbreakable chain of consensus.
When a transaction is broadcast, it first languishes in the mempool, awaiting the discerning eye of miners who evaluate its inputs against the global set of unspent transaction outputs (UTXOs).
The miner who solves the proof‑of‑work puzzle first secures the right to embed the transaction in a new block, and this block, once propagated, becomes part of the canonical chain recognized by all honest nodes.
Because each block carries the hash of its predecessor, any attempt to alter a transaction deep within the chain would necessitate recomputing the proof‑of‑work for that block and every subsequent block, an endeavor that would demand astronomical computational resources.
Consequently, the economic cost of such an attack dwarfs any potential profit from double‑spending, rendering the attack economically irrational.
Moreover, the network’s difficulty adjustment mechanism ensures that the hash rate required to sustain a 51% attack continuously escalates as more miners join the ecosystem.
Even in the unlikely event that an adversary momentarily controls a majority of the hash power, the attack window is fleeting, as honest miners will soon regain dominance, re‑establishing the integrity of the chain.
The protocol also incorporates Replace‑by‑Fee (RBF), granting users the ability to replace low‑fee transactions with higher‑fee alternatives, but this feature is tightly regulated by wallet policies to prevent malicious exploitation.
Merchants, in turn, mitigate risk by enforcing confirmation thresholds-typically one confirmation for low‑value payments and six for high‑value transfers-thereby layering additional security guarantees.
In practice, the probabilistic finality offered by multiple confirmations compounds the attacker’s required effort exponentially, as each additional block demands a fresh proof‑of‑work solution.
Furthermore, the public nature of the ledger permits any participant to audit transaction histories, fostering transparency that underpins trust without reliance on centralized intermediaries.
Thus, the confluence of cryptographic hashing, proof‑of‑work, economic incentives, and transparent verification collectively forms an impregnable barrier against double‑spending.
In sum, Bitcoin’s design embodies a robust, decentralized solution that has withstood over a decade of adversarial scrutiny, reaffirming the durability of its anti‑double‑spending mechanisms.
Benjamin Debrick
October 22, 2025 AT 04:32To put it succinctly, the security model is predicated upon a combination of hash‑linkage, PoW difficulty, and UTXO validation; each component operates in concert, thereby creating an emergent property of resilience-one that resists tampering, duplication, and retro‑active alteration, effectively guaranteeing transaction finality.
Anna Kammerer
October 22, 2025 AT 15:39Oh great, another reminder that you need six confirmations-because waiting half a day is exactly what every merchant loves.
Mike GLENN
October 23, 2025 AT 02:45Honestly, the six‑confirmation rule strikes a balance between security and usability; most retailers find it acceptable for high‑value sales, while low‑risk transactions can often settle with just one confirmation without exposing them to significant double‑spending risk.
BRIAN NDUNG'U
October 23, 2025 AT 13:52Let us seize this moment to celebrate the ingenuity behind Bitcoin’s consensus; the proof‑of‑work paradigm, though energy‑intensive, remains the cornerstone of a trustless system that empowers individuals worldwide to transact without intermediaries.
Donnie Bolena
October 24, 2025 AT 00:59Indeed-its brilliance lies not merely in cryptography, but in the economic incentives that align miners’ profit motives with network security; a truly elegant solution!.
Tom Grimes
October 24, 2025 AT 12:05Look, the whole thing is simple: if you try to copy a coin, the network just says "nope" because the transaction is already marked as spent in the ledger, and any attempt to redo it would need a massive amount of computing power that you don’t have.
John Lee
October 24, 2025 AT 23:12Exactly! The blockchain’s immutable record acts like a neon sign flashing "already spent" for anyone foolish enough to try a double‑spend, and the PoW makes pulling the plug on that sign prohibitively pricey.
Jireh Edemeka
October 25, 2025 AT 10:19Ah, the ever‑fascinating dance of cryptographic hashes-so pretty, yet so ruthless to anyone thinking they can cheat the system.
del allen
October 25, 2025 AT 21:25yeah its like a 24/7 security guard that never sleeps, lol 😆
Jon Miller
October 26, 2025 AT 07:32Nice rundown! It’s cool to see the tech explained without all the jargon.
Rebecca Kurz
October 26, 2025 AT 18:39Sure, but have you considered that the whole system could be a massive illusion-some hidden elite pulling strings behind the scenes???!!!
Nikhil Chakravarthi Darapu
October 27, 2025 AT 05:45The integrity of Bitcoin is a testament to our nation's technological prowess; any criticism is merely noise from outsiders who cannot comprehend the brilliance of decentralized finance.
Tiffany Amspacher
October 27, 2025 AT 16:52Indeed, but one might argue that the very notion of decentralization is a philosophical construct, a mirage that veils the underlying power dynamics inherent in any consensus mechanism.
Lindsey Bird
October 28, 2025 AT 03:59Honestly, this whole article feels like it’s trying way too hard to sound smart-just tell us the basics and stop overcomplicating it.
john price
October 28, 2025 AT 15:05While the prose may appear verbose, the underlying principles are undeniably straightforward: a transaction must reference an unspent output, and the network collectively enforces this rule through cryptographic consensus.
Ty Hoffer Houston
October 29, 2025 AT 02:12Great to see a clear explanation-Bitcoin’s approach to preventing double‑spending really showcases the power of community‑driven innovation.
Ryan Steck
October 29, 2025 AT 13:19But what if the mining pools collude? That’s the real threat no one wants to talk about, and it could undermine the whole system.
James Williams, III
October 30, 2025 AT 00:25The technical details around UTXO set management and mempool behavior are fascinating; it’s where the rubber meets the road for blockchain scalability.
Patrick Day
October 30, 2025 AT 11:32Yo, maybe the whole thing is just a front for the big banks to keep an eye on crypto. Who knows?
Scott McCalman
October 30, 2025 AT 22:39Fact: Bitcoin’s proof‑of‑work is the ultimate deterrent against double‑spending-no amount of cleverness can bypass the sheer computational cost. 😎
PRIYA KUMARI
October 31, 2025 AT 09:45Exactly, and anyone who doubts this is simply ignorant of the cryptographic rigor that underpins the network; they’re not just mistaken, they’re dangerous.
Andrew Smith
October 31, 2025 AT 20:52Let’s keep the discussion constructive-recognizing the strengths while also exploring potential improvements benefits everyone.
Joy Garcia
November 1, 2025 AT 07:59While I appreciate optimism, we must also stay vigilant; blind faith in any system can lead to complacency.
mike ballard
November 1, 2025 AT 19:05It’s impressive how a decentralized network can maintain such robust security; kudos to the developers and miners worldwide! 🌍
Molly van der Schee
November 2, 2025 AT 06:12Absolutely! The community’s collaborative spirit is what keeps Bitcoin evolving and resilient.
Mike Cristobal
November 2, 2025 AT 17:19We should remember that ethical responsibility goes hand‑in‑hand with technological advancement; misuse of any tool is a moral failing. 😊